Black hat growth hacking techniques are not something new. In fact, growth hacking has actually started in the Black cat space.
Some of the well-known growth hacking black hat activities happen, such as black hat SEO techniques, black hat SEO, and blackhead SEO tactics in search engine optimization tricks.
Some popular black hat activities have been SEO black hat techniques; it doesn’t stop their black hat growth hacking from going way beyond search engine optimization. Black hat activities in the growth hacking space started many decades ago.
Unfortunately, the origin of growth hacking comes from black hat activities.
A significant amount of growth hacking activities today still are black hat techniques. However, some of the most potent Rotax are in the grey hat area.
As famously quoted by several people in the cyber security space classify growth hacking is the commercialization of cyber warfare. In all fairness, this statement holds on many levels but not across the whole growth hacking practice.
Before we get started, some helpful background to growth hacking
- What is growth hacking?
- Why is growth hacking important?
- How does growth hacking work?
- When should growth hacking be used?
- How to develop the skills to hack growth?
Subscribe for updates
What is growth hacking?
Growth hackers explore new growth opportunities systematically at any point of the customer journey, from awareness through the market to brand ambassadors by optimizing the product.
In terms of technology, it originated in 2010 when Sean Ellis coined it is mostly used by startups because of its limited budgets and limited resources.
Since then, it has shown an incredible increase in popularization among large-scale and traditional businesses.
Companies like Shopify like Uber has their own head of growth and dedicated growth team. The growth hacker is based on an experiment-based, data-driven.
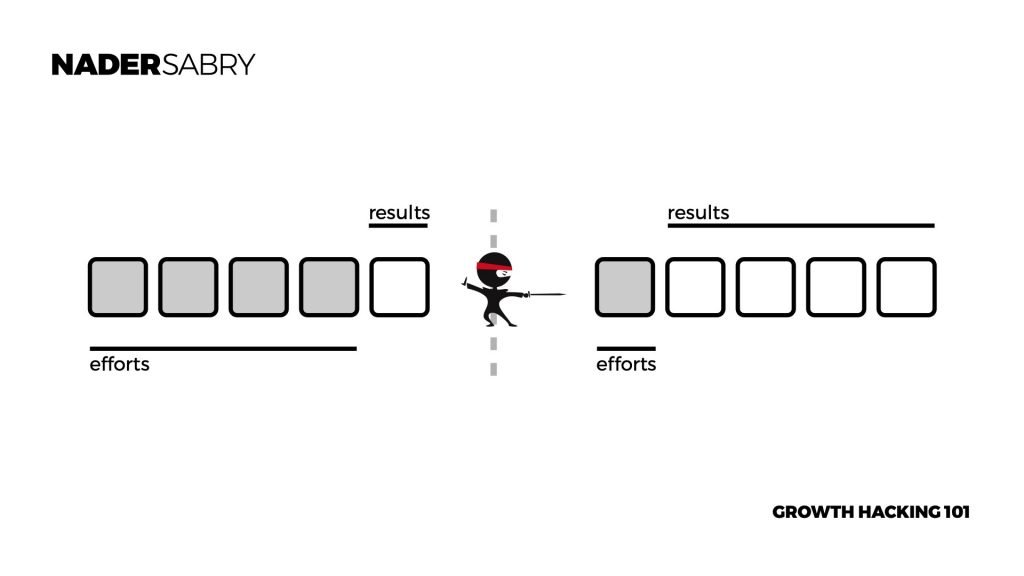
There is a wide range of definitions; in the Book Ready Set Growth, Hack growth hacking is defined at a strategic level as a process that achieved disproportional results.
This is best understood through an example of efforts v.s results. This is when less effort is exerted to get dispositional results. Growth hacking works that simple.
Not just in top tech companies run by silicon valley’s top entrepreneur making hundreds of millions of dollars daily, shaping silicon valley’s culture, and defining the new silicon valley entrepreneur.
As many growth professionals leave the traditional marketers behind, a new breed of growth hackers is emerging.
How does growth hacking work?
The Ready Set Growth Hack defines growth hacking as a systematic process governed by the growth cycle concept. the growth cycle is a three-phase process, where it starts with a growth problem, moves into experimentation then into scaling.
Based on this process, once a growth problem is well defined through a specific process, it would then be up to the growth hacker to find solutions. Solutions are found vis structured and systematic experimentations.
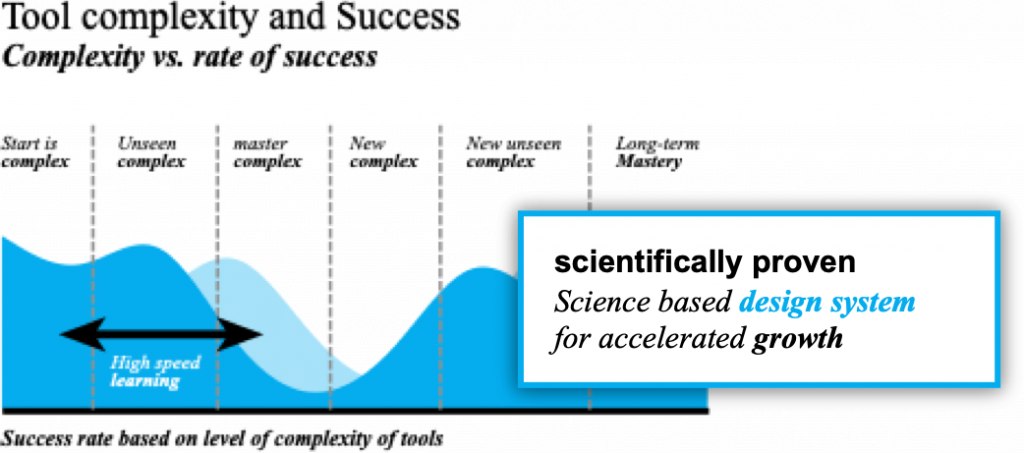
Using growth analytics for data-driven growth decisions, growth hackers can quickly discover what works and doesn’t before investing a penny in more development. This is governed by a process called growth thinking which is a design methodology used for growth hacking.
Break the rules – growth hacking
The hidden weapons of growth hacking are simple and simple: Be a rule-breaker. The job requires you to think outside the box and unleash your creativity. A growth hack involves having the right mindset on growth.
This job requires creativity and ad-hoc experiment with hypotheses and high potential. Be creative growth Hacks won’t come with any rules. Rule-breaking is at the core of growth thinking and how the growth hacking process works.
- if a rule is working, find a better way to break I
- If a rule isn’t working, break it with a better one
- If a rule is about to fail, let it and then break it
- If a rule is about to have success, break that too
The growth hacking mindset or growth mindset is a very different way of working than that of other professions. Their goal is the north star metric which is basically a growth goal and only a growth goal.
Black Hat Hackers – back hat growth hacking tehcniques
Hackers often have deep experience of hacking into computer networks to bypass the security measures on the network and hack the systems themselves.
Their primary motive is financial or personal gain, but sometimes they are also involved in cyber extortion, protest, or just addicted to cybercrime.
Not only do Black Hat hackers want to steal, but they also want to destroy data. These can range from amateurs who got their feet wet by spread malware to experienced hackers who aim to steal financial information, personal information, and login credentials.
They are also responsible for writing malware, an approach for gaining access to the systems they are using. However, some companies seek to copy, manipulate or delete data.
In conclusion, black hat growth hacking activities are illegal, immoral, and ethical. Black hat activities are breaking the law and always. Often dolls in gauging in cyber warfare or black hat activities initially start with good intentions.
Their primary driver is to test the capabilities to see how they can break systems. They break the systems without creating any harm to expand the potential capabilities they have.
When this forms into a habit, whether able to break into systems using black hat techniques, they now start to identify potential advantages. The corner of these advantages that they discover has a commercial implication.
It becomes dangerous and illegal when they discover how to exploit these commercial interests using black hat techniques and general hacking.
Black hat SEO techniques in the black hat SEO area are extremely lucrative. Some examples used in this area are illegal or black hat hackers acquiring plug-ins in some of the most popular platforms like WordPress and manipulating traffic through embedded code to their own websites.
Black hat SEO techniques in the black hat SEO are heavily undertaken because of their commercial viability. Still, more importantly, they are the most lucrative part of the hacking spectrum.
Although black hat SEO techniques and black hat SEO are illegal, black hat SEO is a multi-million dollar industry and is not going to end overnight.
Black hat SEO techniques in the black hat SEO space or becoming more sophisticated; in fact, cybercrime entities are having a lot of trouble dealing with these guys.
Black hat SEO techniques will continue to thrive as long as they are commercially lucrative, which is the case today and will be for a while into the future.
Subscribe for updates
Grey Hat Hackers and growth hacking tehcniques
Grey Hat Hacking is a hybrid of black hat and white hat activities. Normally gray hat hackers will look for hacking weaknesses for computers without permission or knowledge. When problems are found, owners will notify them and sometimes charge for the fix. Even if the property owner refuses it, the hackers sometimes upload the new exploits to the web for free.
This type of hacking is still considered illegal because a hacker received no permission from the developer before attempting to hack the network. These kinds of hackers are not inherently malicious in their intentions. They are seeking to extract something from their discoveries.
In conclusion, as you can imagine, grey hats, a hacker is a grey area. This means that parts of it could be legal and other parts could be illegal under part in the middle that is not defined either as legal or even illegal. They are often best known for grey hat SEO but don’t stop there.
This middle part is where a lot of the magic happens for some of the top growth factors on the planet. We referred to this as greyscale, and greyscale ranges from dark to light. But we have found is darker activities on the greyscale are more potent than those on the lighter side of grey.
Search engine optimization is one of the key areas that is being tackled in the area of grey hat activity because the commercial implications of tapping into free traffic that already exists are commercially viable and extremely commercially lucrative.
Black hat SEO will not stop; it will continue like this for a long time.
What are White Hat Hackers and growth hacking tehcniques
White hat hackers can perform penetration tests, conduct security assessments in-house, and carry out security assessments and exploits for customers.
These are often paid employees or independent contractors who work for companies as security specialists and attempt to find security holes through hacking.
And there are even courses, training, and certifications for ethical hacking. White hacking has the same methods as the black hat, with only one exception. In short, they do it first with a permit from the software owner, which makes it fully legal in the United States.
What is black hat SEO?
Black Hat Marketing is generally defined as a disapproved behavior that can raise a page’s ranking on a search engine results page.
These practices are contrary to the website’s terms and conditions of service and can cause the site to be deactivated from search engines and affiliate lists. Bing publicly condemned Google Webmaster Guidelines over the issue. Does my work add value for the user or for search engines to see?
Black hat SEO is a thriving industry that is not going to go away any time soon. If anything, black hat SEO has become even more difficult to detect, and two in force legally buy some of the largest players in the world, including companies like Google and Microsoft.
Cybercrime experts have stated that black hat SEO activities or a gateway activity to several other hacking activities. That said, they have also classified black hat SEO activities as one of the most commercially lucrative cybercrime areas.
The black hat SEO is commercially lucrative in tapping into existing traffic of people who are ready and willing to spend money. By tapping into traffic capabilities using black hat SEO, a cybercriminal can identify the intentions of somebody ready and willing to spend and put their proposition before anybody else. This black hat SEO technique is extremely lucrative.
Why is Black Hat SEO risky?
Avoid the black-hat SEO techniques to gain long-term visibility in the search results. Use ethical and sustainable standards and methods of SEO. Black Hat SEOs affect your online presence in multiple ways.
Black hat SEO activities are illegal if you are cut; the price to pay is very large, including going to prison in most countries.
The risk being taken goes way beyond that; in many ways, black hat SEO activities of all are commercially very lucrative; they are also, on the other hand, a massive commercial risk to some of the largest players in the tech industry. Black hat SEO oh activities by cybercrime experts are classified as gateway activity.
Although we have highlighted the commercial benefits of black hat SEO, it also has national security risks. Intelligence agencies have used black hat SEO to use a light form of commercial interest to open up sensitive national security secrets.
This is an activity highly monitored by the CIA and the NSA in the equivalent of such counter-intelligence agencies in the world.
The problem with black hat SEO oh, it is a straightforward way for people to fall into his trap. One of the commercially viable categories in the area of black hat SEO is dropshipping.
Dropshipping is an e-commerce technique where is the provider does not own the product was the brand but generates the sales and then pushes it through for a commission.
Black Hat SEO vs. White Hat SEO
Black hat SEO will never change search algorithms in Google search rankings to improve a user’s online search experience for search engine rankings. It can result in being totally wiped or getting a lower ranking.
The white hat SEO is aimed toward creating high-quality SEO and good user experiences. This article tells you how SEO hacks should be handled to make your organic search strategy more effective.
What is white hat SEO
white hat SEO is an SEO technique based on techniques in line with search engine optimization. Google’s webmaster guidelines, for example, is one of the main guidelines used for search engine white hat SEO techniques.
Black hat tactics in Google’s webmaster guidelines clearly state. What they are in a few different ways. They need to keep their services fair and protect everyone using them, including an even playing field. Google’s guidelines are clear, and the industry-standard is used across all major players.
Subscribe for updates
27 Black hat SEO tactics
Black hat SEO tactics are not something new it’s been practiced for decades. Some of the black hat SEO tactics used are some of the following black hat SEO tactics:
01. Plagiarized or duplicated content
Unauthorized use could breach trademark legislation. Why should Google remove plagiarism? Google was working hard to crack down on plagiarism to prev. This is a widespread form of black hat SEO tactics. This helps manipulate search engines.
02 Spamming Blog Comments
Marketers using black-hat SEO can comment on numerous websites. It’s like Black Hat Web Search Engine Optimization in that it attempts to gain links. Another way to manipulate search engines
03. Abusing structured data
Structured data is a script that relates the content of the site to given information content. Black hat SEO manipulates structured data, so search engines display distorted information on search engines.
04. Rich Snippets Spam
Rich snippets are small snippets of extra info. More information may drive more traffic. There are many ways that schemas can be manipulated. This is one of Google’s entire pages dedicated to support.com about this feature. A great way to fool a search engine. This also helps with keyword stuffing.
05. Footer Links
Footer is key real property for a link because footer advertisements come out of every website page. Google will most likely find them and penalize them for using commercial anchor text for research.
Suppose you added a link to the footer with keywords to trick the search engine. Also knows as keyword stuffing.
06. PBNs
WebRINGS are classified as merely link schemes when they manipulate algorithms. PBNs are used much more frequently in the early 2000s, particularly among fan pages for various shows, films, musicians, etc. Webring isn’t necessarily a good thing, though.
07. Publishing a bunch of low-quality content
Many black companies try to beat the system by releasing low-quality content. Instead of black hat tactics, create meaningful and valuable SEO articles that answer your search intent to readers. Good content isn’t easy to create. It’s worth creating good content for your readers.
08. Negative SEO or falsely reporting competitor sites
This technique is used to impose penalties for competing sites that use search engines. Making it appear like other sites are performing black hat SEO is 2 unsavory practices. Black Hat search engine optimization is used on websites to make it seem like a competitor’s website uses a black hat strategy.
09. Malicious Backlinks
In a bid to promote SEO, Black Hats may use google penalizes to promote his business agenda. This is why Google created this page so that you can disavow those links.
It helps you do background searches and then removes yourself entirely from any undesirable sites to which you linked. Google’s website aims to make it easy for users to remove unwanted content.
10. Doorway/Gateway pages
All of the content you upload should provide a goal Google says. A site created solely to respond to specific search queries and use the content as purely one page is considered to violate the guidelines by Google.
These kinds of pages are often called a gateway or portal pages. Create content for humans and not search engines, and you shouldn’t create pages to rank for keywords you aren’t into.
11. Hidden links
You might be thinking about hiding some links by allowing them to remain visible in the text of a website. Google would like to note you and punish you when you’re trying to cheat. If you list enough useless links somehow, you could easily discourage Google from directing traffic to their targeted audience because your page’s importance would diminish.
Deceptively hidden links are against the guidelines outlined by Google. You’re not going to hide links here! These hidden kunks help with keyword stuffing.
12. Paid/Manipulative Links
Links are one of the common types of black hat SEO. The Bottom-up is that links should be earned particularly as they’re editorial ratings that trust the website. This means you must avoid techniques like hiding text or hiding links.
The best way to hide a reputable link from content is to avoid using tactics such as hiding a URL inside the content. Avoid strategies such as hiding links hiding articles, and hiding information from the internet. The use of linked schemes and/or hiding things.
13. Hacked website
Unsecured websites cannot technically get you a penalty by Penguin / Panda. This can cause Google to find hacked sites on the search engine. If your site is compromised, you may lose important links and visibility.
Google could block your website if they know your website has been hacked or if you infringe on your search engine’s results. Even your website loses its credibility to Google. Nonetheless, Google tries to keep you safe, but you will see an impact a Penguin penalty. More information see: [link].
14. Groupon’s Bait and Switch
Groupon has been blamed for doing a bait and switch by San Francisco Comprehensive Tours. The voucher websites still advertised the promotion on Google long after the promotions had ended.
Groupon has not revealed any discounts that searchers could find after the site was changed out. I’m guessing the results came from a search. Usually, the bait/switch occurred on PPC – advertisements. But these happen on organic – results too.
15. Bait and switch
Why should you change your content to make your site rank higher? The first step is writing a webpage for Google with a set of keywords and, after it ranks, the author changes it with another project or product.
This cheesy method to trick Google has certainly worked well in the past, but it now would bring you banned, and in case of hit the lottery, your rights will be challenged in court. In 2011 Groupon used ‘’Bait and Switch’ on Search Ads and was accused of running shady and misleading operations in San Francisco.
16. Buying backlinks
Black hat marketers may pay websites for links to increase rankings on search pages. Linking a site is considered part of an off-page optimization process that can boost site rankings.
17. Malicious Active Content
There are also malicious software programs installed through animated websites, Java applications, Javascript, Flash content, or browser plugins to display and download videos. The most common types are the most common types of malware like adware bots, virus worms, rootkits, etc. The actions taken in this regarding against Google guidelines; will take you into a high liability. It is illegal in a way legal.
If you’re using, the best way to avoid a potential breach of this protection is by downloading files from unknown websites and not by using suspicious sites.
18. Keyword Stuffing in Alt Tags
Alt tags allow you to write keywords as easily as possible, but the risk is small. But in that context, it may damage the website’s rankings. Alt tag is: Alt tag, TagTag keywords and TagTags. You would also misuse alt keywords which essentially damage you yourself and/ or your visit.
19. Keyword Stuffing and Duplicate Content
This is the use of an inappropriate keyword or wording to gain the attention of search engines as they index the site for the relevant keyword. Duplicate material is copy-pasting similar material over numerous websites to attract search engines.
The other tactic generally runs against Google’s guidelines. Instead of copycat and keyword stuffing, use keyword-optimized best practice techniques and the copycat checker to ensure your pages get the necessary signals to search engines. Rather than keyword shopping, use keywords optimization best practices and keyword optimization.
20. Clickbait
Clickbait is an eye-catching and misleading headline written only to make you click. In the headlines, something else happens on the site. Using this manipulative technique will negatively affect your CTR, and ultimately a website will suffer greatly.
Click baits allow a user to earn more income through clicks on websites. These techniques are viral in tabloid papers, where they spread rapidly. The purpose is to de-prioritize posts with headlines that show information and engage you to click simply so you can know. Facebook has said they want to ban clicking bait.
21. Content Automation
Content automation means applying an automation script to generate content that anyone in the world can then access.
This automated content is written with no intention for the user and has nothing format or style whatsoever without pictures, HTML headlines, paragraph spacing, alignment, etc. You start experiencing significant rank loss keyword cramming risks and even blocklisted from search engines.
There are tons of tools to do your dirty work, but you can think about the consequences before taking action. You could try BrandMentions to inspire your brand to create organic traffic and rank.
22. Link Farm
Links to other websites can manipulate your links profile by growing the number of links inbound. It may cause a bad impact since Google looks at link farming in a spammy way. A website participating by a link farm will show the same content like any other website you might come across in your browser, except this website is covered with inappropriate hyperlinks linking randomly.
This practice is also penalized if you create not natural links but are not considered natural links when they can easily be created in a site’s content engine. Humans do not exchange such links but rather use search engines.
23. Using misleading redirects
In this version, false redirects are set, which leads people to different websites. Another solution would be sending a high-quality page to a shallow quality page to increase its search rankings. False redirects are another black hat trick used to misleading audiences and user searches.
24. Sneaky Redirects
SEO in black hat sites utilize redirect messages outside their intended function. This may include redirecting a search engine crawler to one page and all other users to another. A 303 redirect provides authority between a site page and a page. It also means something which works in black hat SEO could only change the redirect on their Google page.
And sneaky redirects are to be avoided. They do not follow google nor Yandex guidelines. It is also possible to use JavaScript occasionally to redirect users. Give an example: LinkedIn redirects you to someone’s full profile when you are registered.
25. Hidden text
Hidden text is the same text color as a background displayed off the screen or behind an image. These words are misleading but use them to pack keywords inside. The hidden text does not apply to text in an accordion on a tab or is loaded dynamically using JavaScript. Web search engine crawlers now understand keywords.
From our side, there is no point in including the hidden language in your pages on your website. We are not talking about hidden text completely, but it doesn’t mean that all text is hidden in accordion or tabs or loaded dynamically.
26. Hidden Content
Hidden content is content that is produced in the same coloring as its background. It aims at including as many keywords as possible within a page. A Google algorithm can distinguish between keywords within a paragraph from those hidden in its context. Content is invisible, and users and search engines can easily find it.
However, not all hidden contents are forbidden in certain circumstances as much as these are visible to users, search engines, and mobile users. An example may involve content that can be hidden on a PC display but only accessible via mobile. Generally, the content must clearly appear in the view of the user.
27. GuestPost Spam
People who send emailed requests for guest blogging on a site can affect site rankings if the site they link can have a poor customer experience.
In 2014 DocSheldon.com was charged a manual sitewide penalty from the user if the site has an inbound link from a guest post to an unknown site. You must provide information that will help the audience then return it with traffic and not irrelevant links that will take off for good.
Don’t be among bad guys that send out anonymous messages to writers and post posts with links to be featured on your list or for free! The former head of search engine Google was discussing its Webspamm campaign with Google over Twitter in 2014.
Subscribe for updates
It is best to avoid the black hat SEO techniques.
Avoid black hat SEO at your best. As tempting as it might be, it comes with a big price if it doesn’t work and when caught.
Keep in mind that big tech companies like Google and Microsoft consistently upgrade and change their algorithms daily to avoid any black hat SEO activities taking place.
The algorithms are becoming a lot more sophisticated in detecting, identifying, and holding doors could you break the rules accountable.
Black hat SEO activities, for the most part, are a short-term play; in the long term, they will not work because of the updates to come into the algorithms. In fact, it’s best to report black hat SEO, and often the big tech companies reward report black hat SEO activities.
What are white hat SEO techniques?
White hat SEO techniques are essentially SEO techniques that follow the search engine guidelines. The search engine guidelines set the rules for search engine marketing.
The objective is how to safely and fairly work towards search rankings. Search rankings are about how well you seem to be visible in a search for keywords. Search rankings are core in the search engine guidelines.
The guide defines what the black hat tactics that are not allowed are. Black hat tactics play a big role in the guide; it defines the black hat tactics and how to avoid being penalized.
They cover things like own site techniques, paid links, link scheme, link building, unnatural links, commercial anchor text, usage of anchor text, buying links, links pointing, high-quality content, and a good way to generate traffic. They also look at things like poor user experience and how to overcome a poor user experience.
Irrelevant keywords are also another area they guide, enabling you to nest work the keywords that matter what they define as black hat practices and how they penalize it. This is well covered in the search engine guidelines.
High-quality content is an important part of the guide where they literally State the dos and don’t of the rules that they use to define and qualify what is high-quality content and what is not high-quality content.
===========
Introduction to growth thinking — growth by design, how to thinking design, and growth hack.
GROWTH BY DESIGN – Most Growth Hackers struggle to get traction for new ideas. A lack of guidance and exact next steps are to blame.
Imagine if you could grow a new concept from beginning to end, with a framework to move from thought and action in a fast, simple, and low-cost approach. Actioning ideas with precision isn’t easy; with the growth thinking, science-backed design system built by the top minds in growth hacking, it’s a simple, well-structured yet creative system that allows you to find growth.
Growth thinking is a fast, easy, and simple way to prototype growth hacks. This enables growth by visualizing a growth hack in abstract and then detailing them into a systematic approach. This makes it easy to develop and improve growth hacks and generate new, better growth hacks.
.





